Zero-Trust Execution Mesh


Data into Trust.
Mission Statement
ZTEM eliminates implicit trust and enforces policy at the data boundary using self-verifying cryptographic capsules. It treats every packet, message, and transaction as hostile until proven otherwise. Each data element carries its own cryptographic policy, lineage, and verification signature. Security travels with the data, not with the network
Doctrine Overview
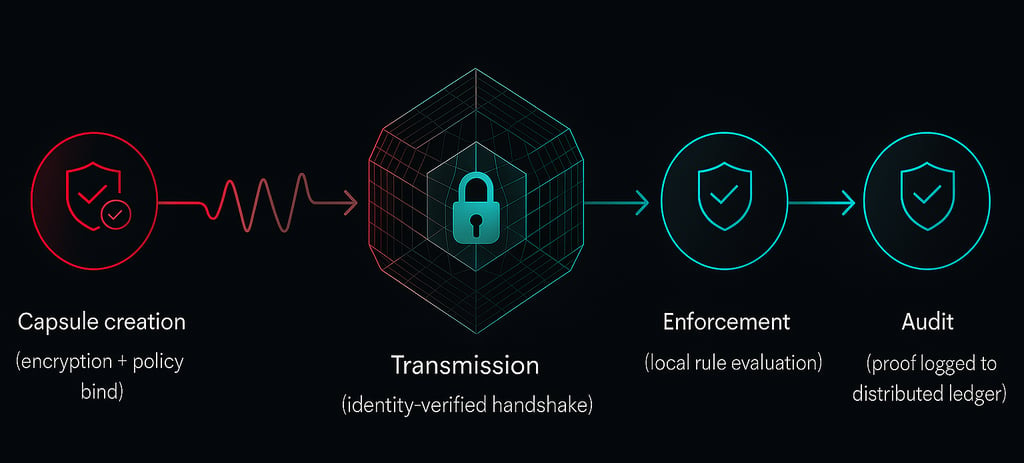
Core Mechanisms
Ephemeral Identity Binding
Tokens generated per session using OAuth2 short-lived JWTs tied to hardware TPM or biometric identity.
Cryptographic Capsules
Data encapsulated with ML-KEM (key encapsulation) and ML-DSA / SLH-DSA (signatures) ensuring post-quantum resilience.
Policy Enforcement at Edge
Attribute-Based Access Control (ABAC) rules executed locally with deterministic outcomes, even offline.
Verifiable Logging
Each decision and policy execution recorded as a Merkle-linked hash chain, tamper-evident and auditable.
